AWS SNS
AWS SNS + Pulse Integration Benefits
- Alerts triggered by Pulse will be forwarded to AWS SNS and retrieved by consumers.
How it Works
Pulse events that arise from metrics that go beyond threshold, anomaly detection, misconfiguration etc of monitored clusters send an event to an SNS topic. This topic can then be subscribed to by consumers such as SQS or e-mail. See https://docs.aws.amazon.com/sns/latest/dg/welcome.html.
The alert message published to SNS is JSON-encoded and wrapped under the default key. Here is a sample message received:
{
"default": {
"timestamp": "2024-06-01T10:12:45Z",
"subject": "High CPU usage detected",
"text": "CPU usage exceeded 90% on node-4.",
"severity": "critical",
"cluster_name": "production-cluster",
"cluster_fqid": "org-123/cluster-abc"
}
}
Requirements
- You will need access to view the specific cluster in Pulse. If you do not have this access, contact an Admin or Account Owner within your organization to configure the integration.
- Pulse requires an the SNS Topic ARN to write to as well as access key and secret key of a user with a permission to publish to that topic. Alerts and incidents must be enabled for the cluster in Pulse.
Set Up AWS SNS
Follow these steps to integrate with AWS SNS. The links to AWS documentation explain how to create the relevant assets in the console. In the bottom of this page you will also find relevant terraform code.
- Create an SNS topic and add subscribers as necessary. Document the ARN of the SNS topic. You can do this via the console as explained here: Getting started with Amazon SNS. If you've subscribed to the topic with an e-mail address it is recommended you confirm the subscription before setting the topic up as an alert destination.
- Have an access key/secret key ready, or create a user with an access key or add an access key to an existing user. Keep in mind that a user only gets to have two separate sets of access keys at a time. Managing access keys for IAM users
- Make sure the user has permissions to publish to the SNS topic. This can be achieved by either attaching a policy with the sns:Publish action directly to the user or attaching it to a role and having the user with the access key id in its assume role policy. A basic tutorial: Setting up access for Amazon SNS
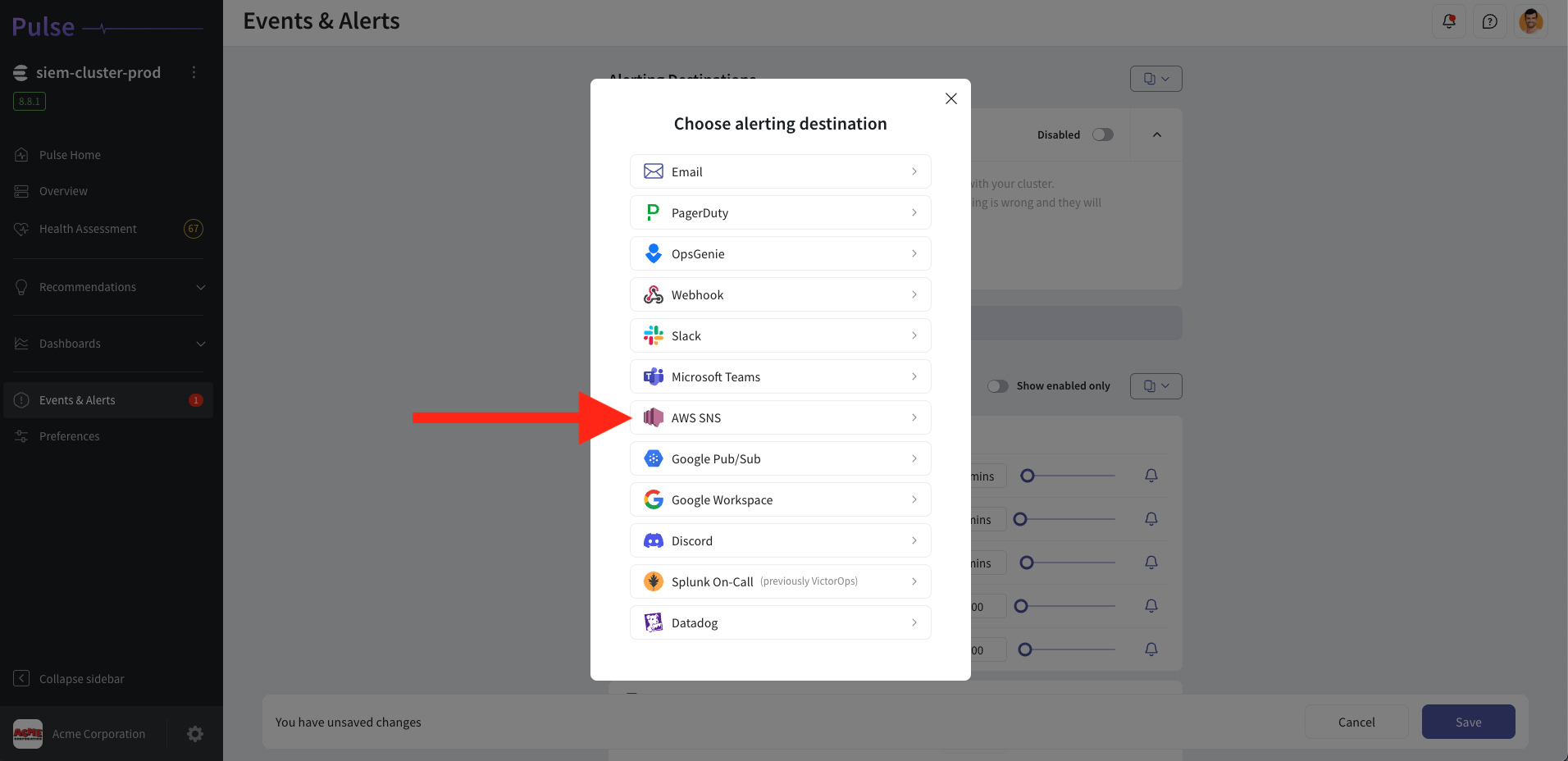
Create an AWS SNS Alert Destination
- Log in to Pulse and navigate to the monitored cluster.
- Go to Preferences > Alerts Destinations.
- If no AWS SNS destination exists, click + AWS SNS.
- Ensure you have set up your AWS SNS topic and credentials as described in Set Up AWS SNS.
- Provide the Topic ARN and the security credentials.
- Set the desired alert severity to trigger AWS SNS notifications (recommended: critical only).
- Click Save Changes.
Disable the AWS SNS Alert Channel
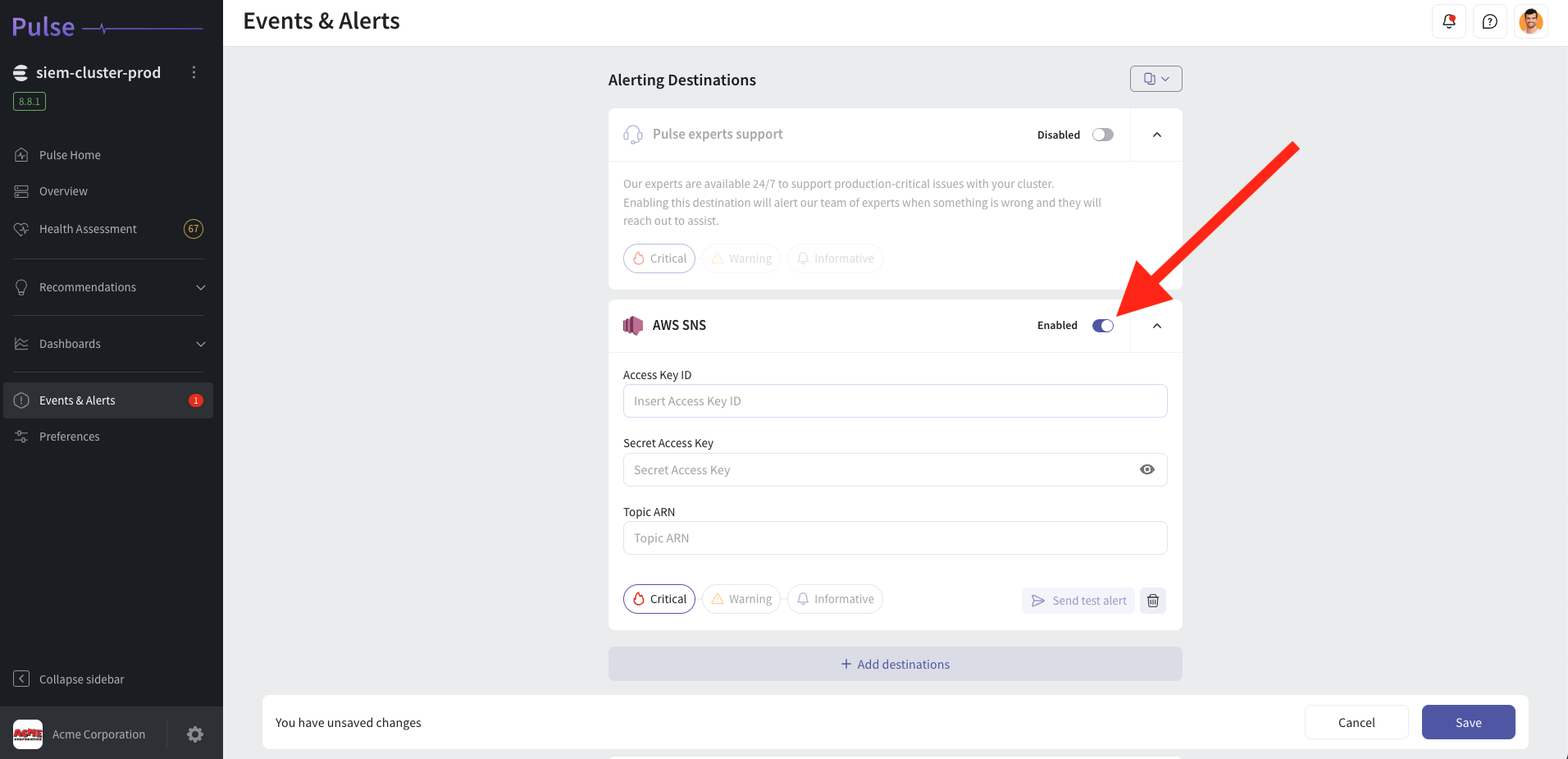
Follow these steps to disable the AWS SNS alerting destination in the Pulse Console.
- Log in to Pulse and navigate to the monitored cluster.
- Go to Preferences > Alerts Destinations.
- Disable the AWS SNS Alerting Destination by toggling the "enabled" toggle.
- Click Save Changes.
Uninstall the AWS SNS Alert Channel
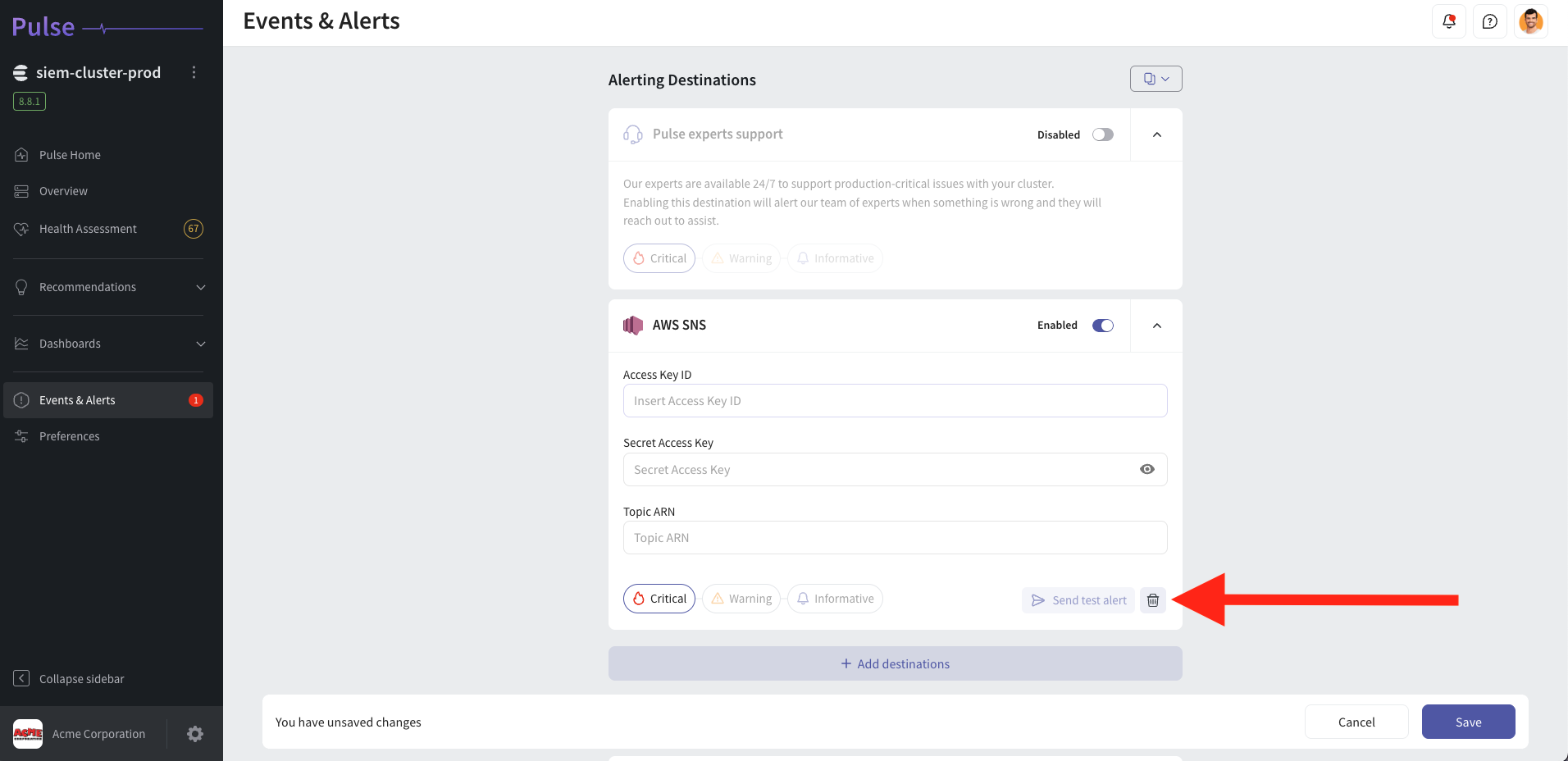
Follow these steps to uninstall the AWS SNS alerting destination from the Pulse Console.
- Log in to Pulse and navigate to the monitored cluster.
- Go to Preferences > Alerts Destinations.
- Remove the AWS SNS Alerting Destination by clicking the Remove icon.
- Click Save Changes.
Terraform code
main.tf:
provider "aws" {
region = var.aws_region
}
resource "aws_sns_topic" "pulse_alert_test" {
name = var.topic_name
}
resource "aws_sns_topic_subscription" "pulse_email_target" {
topic_arn = aws_sns_topic.pulse_alert_test.arn
protocol = "email"
endpoint = var.email_address
}
iam.tf:
resource "aws_iam_access_key" "snskey" {
user = var.user_name
}
data "aws_iam_user" "pulse_user" {
user_name = var.user_name
}
resource "aws_iam_role" "pulse_sns_role" {
name = "pulse_sns_role"
assume_role_policy = jsonencode({
Version = "2012-10-17"
Statement = [
{
Action = "sts:AssumeRole"
Effect = "Allow"
Sid = ""
Principal = {
"AWS": "${data.aws_iam_user.pulse_user.arn}"
}
},
]
})
}
resource "aws_iam_role_policy" "pulse_sns_role_policy" {
name = "pulse_sns_role_policy"
role = aws_iam_role.pulse_sns_role.id
policy = jsonencode({
Version = "2012-10-17"
Statement = [
{
Action = [
"sns:Publish",
]
Effect = "Allow"
Resource = "${aws_sns_topic.pulse_alert_test.arn}"
},
]
})
}
output "secret" {
value = aws_iam_access_key.snskey.encrypted_secret
}
For support please contact hello@pulse.support.